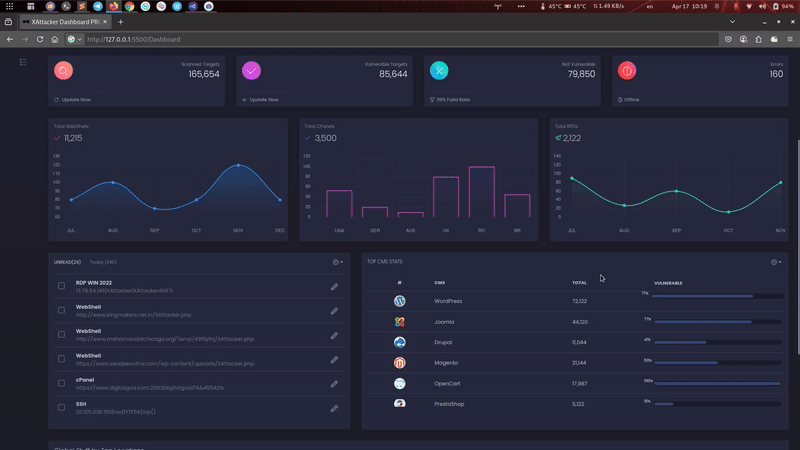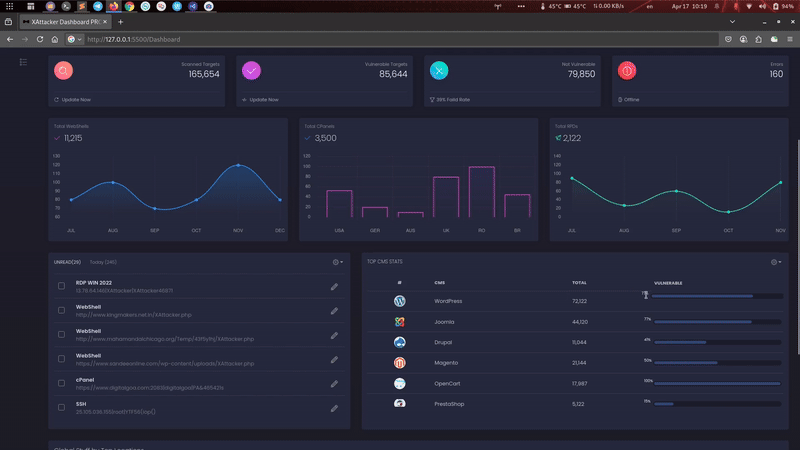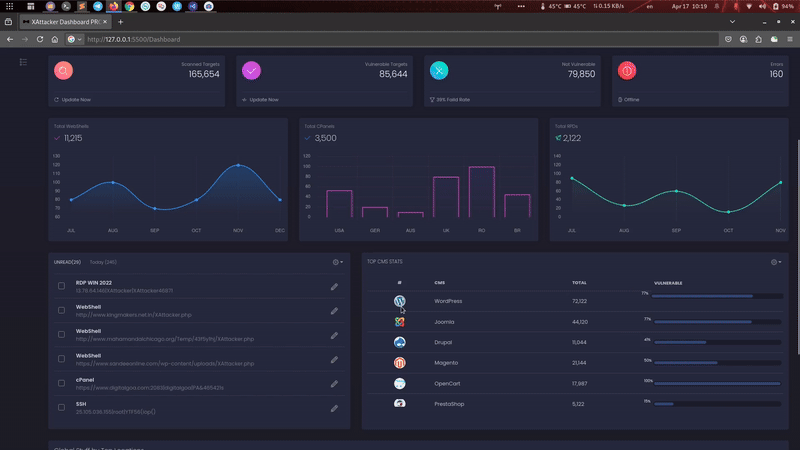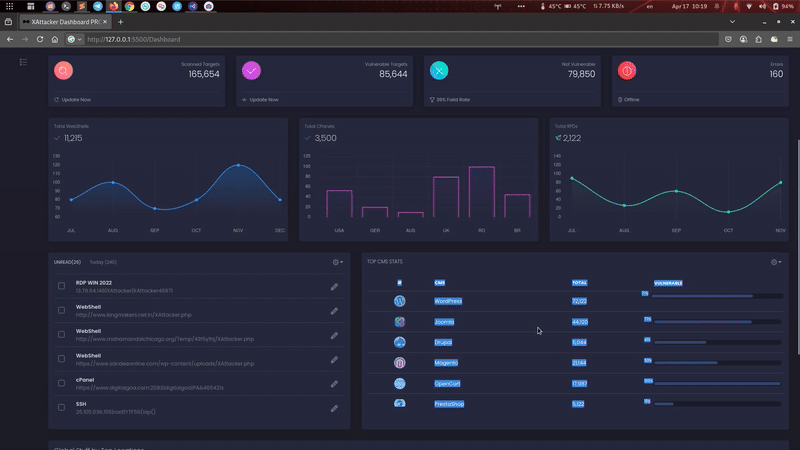
XAttacker V50 PRO
The most advanced Penetration Testing Distribution. Ever.
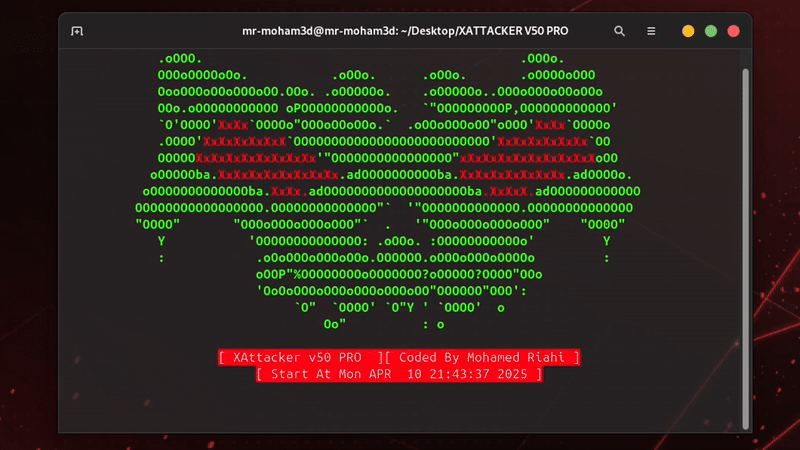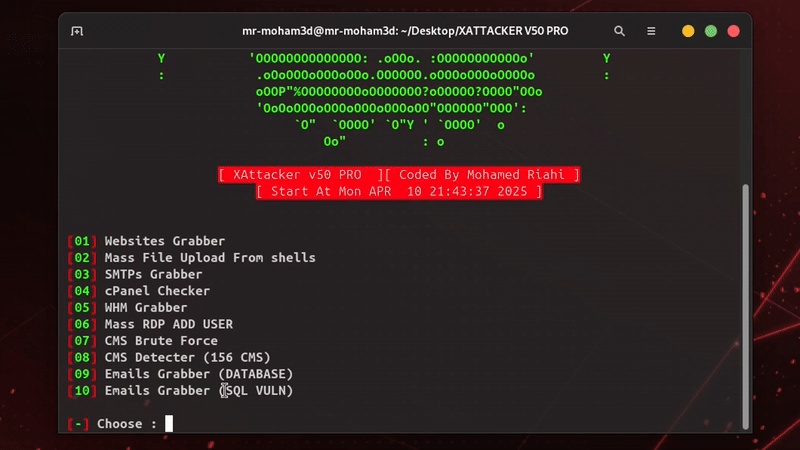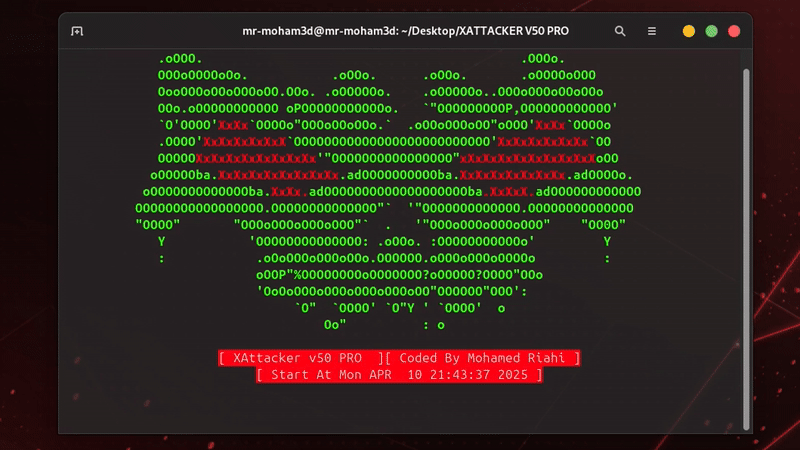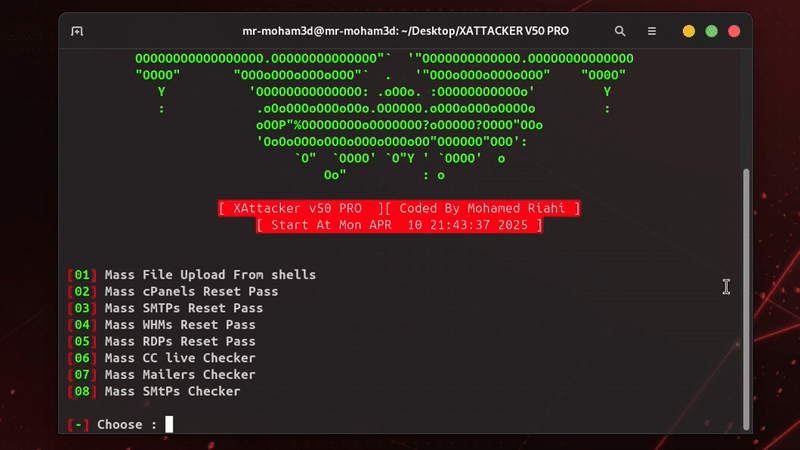
XAttacker V50 PRO
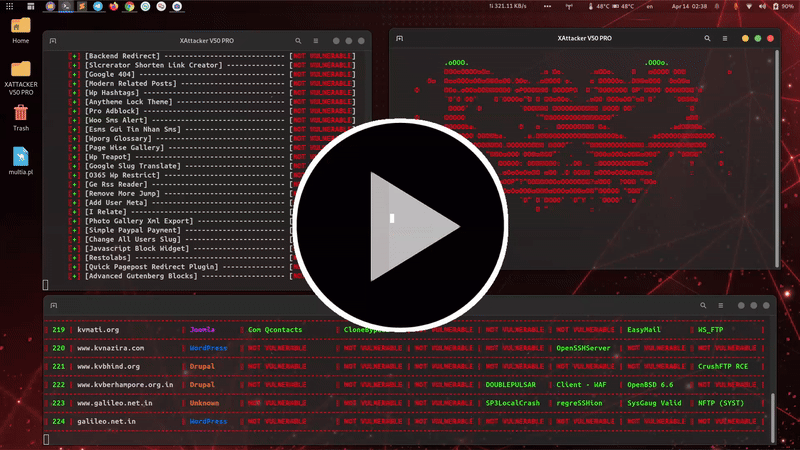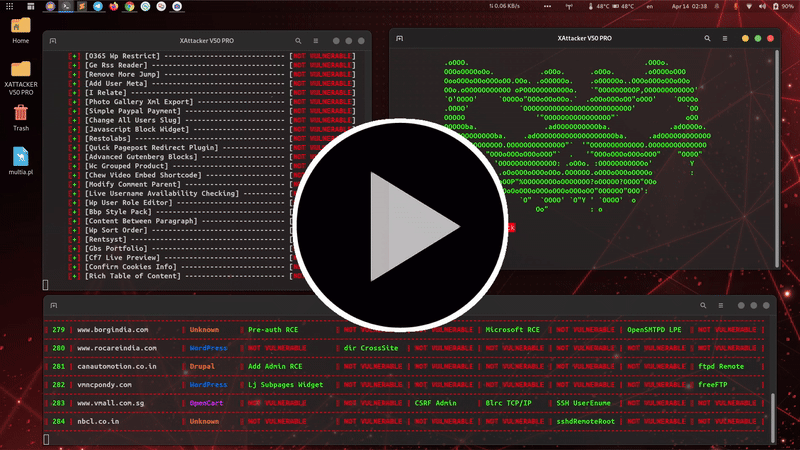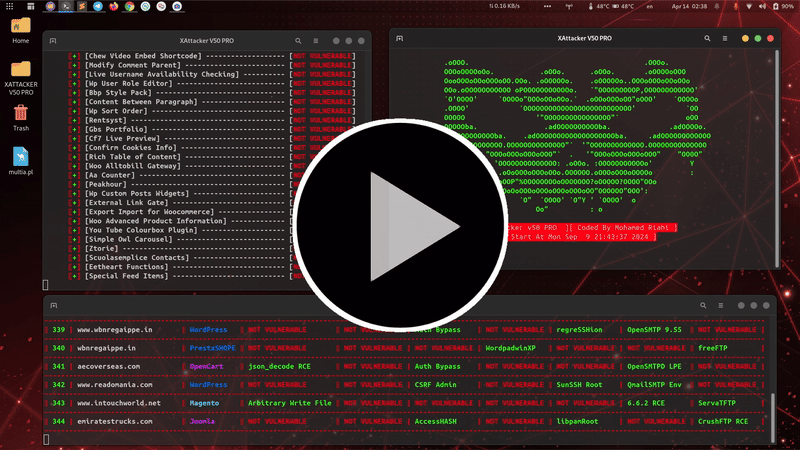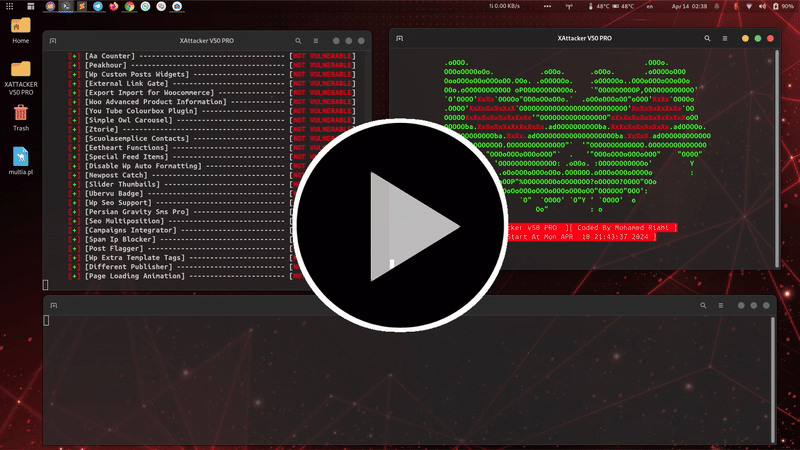
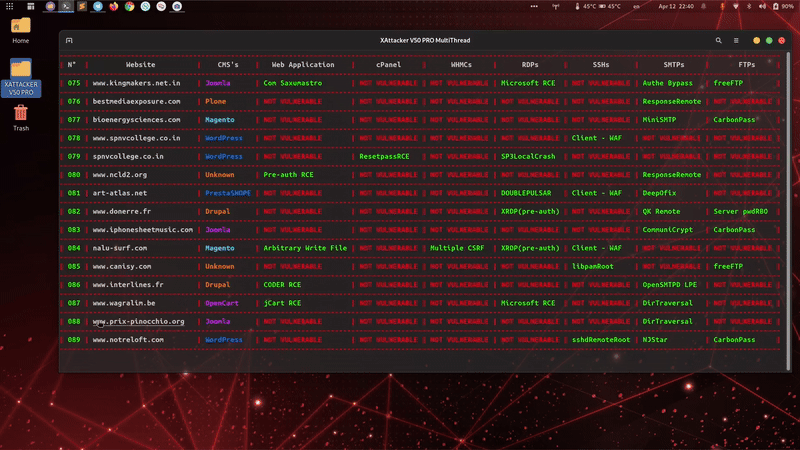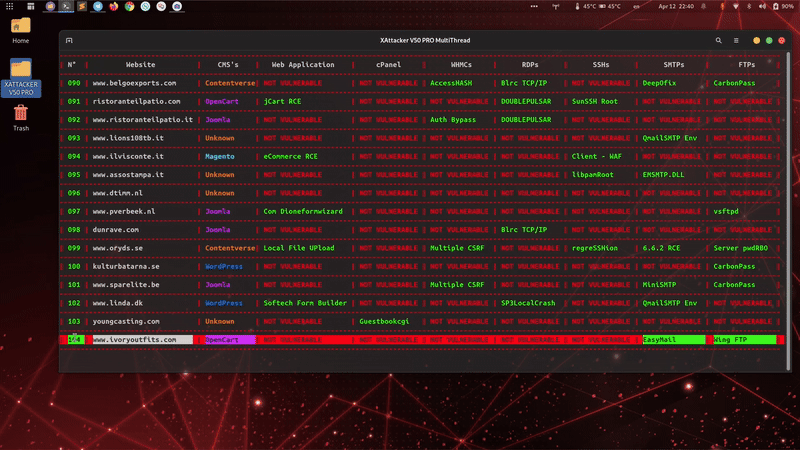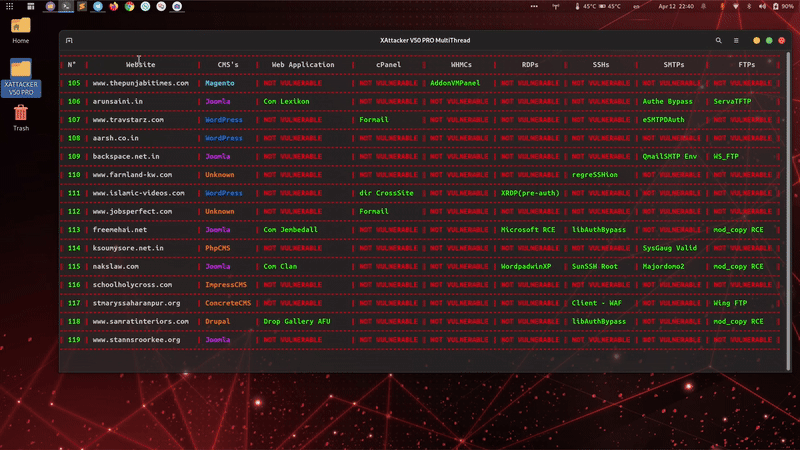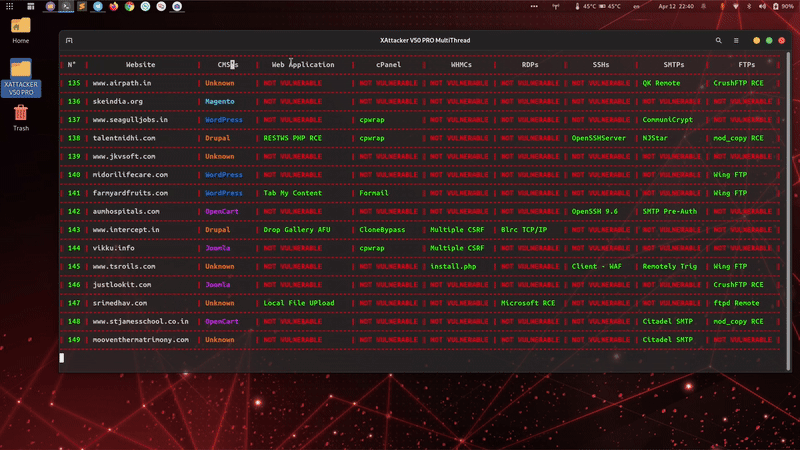
is a professional, high-powered exploitation tool designed for scanning and automatically exploiting vulnerabilities in web applications. By simply providing a target URL, XAttacker analyzes the website’s architecture—especially if it's built on a Content Management System (CMS)—and identifies weaknesses based on the detected platform. Once vulnerabilities are found, XAttacker automatically generates a working exploit tailored for the target and delivers a direct link to the user, streamlining the entire penetration testing process.